Cyber-attacks are no longer just a focus area for large financial and tech institutions. These attacks are becoming more common, targeting various institutions in a variety of different sectors. SME`s might not be classified as high-value targets, but the chances of successful attacks are compounded by the fact that SME’s don’t generally prioritize cyber security. Limited time and resources are spent on preventing attacks, and even less time on how to respond in case of an attack.
Businesses of all sizes must plan for these events as the risk associated with cyber incidents are growing year on year. During a cyber-attack, the focus should be on containment, eradication and recovery. Without a well-documented, thought-out plan, the chances of managing an incident to a successful outcome become negligible as there will not be time to build the incident handling process while the crisis prevails.
Cyber Readiness is Required
An incident response plan offers several potential benefits.
Fast turnaround on mitigation
Having a plan will help an organization minimize its response time because all role players will know and understand what their responsibilities are and what the process is that needs to be followed without having to re-invent the wheel. A delayed response means the attacker has more time on your network to gather sensitive data, infect other systems and cause disruption to your business processes, which will take longer to fix.
Organized approach
An incident response plan allows efficient and effective use of manpower, tools, and resources to tackle the incident with minimal disruption to the business. This cuts the cost of managing incidents significantly.
Regulatory Compliance
As governments start to feel the impact of cyber incidents, we are seeing more regulations entering the market. This places a significant burden on companies as they must ensure compliance or face significant fines. Protection of Personal Information Act (POPI Act), General Data Protection Regulation (GDPR) and Payment Card Industry Data Security Standard (PCI DSS), are examples of such regulations under which organizations need to have an incident response plan to ensure compliance.
Disaster preparedness
By proactively identifying threats and mitigation actions, companies can plan actions in advance and ensure the availability of resources to deal with the threats.
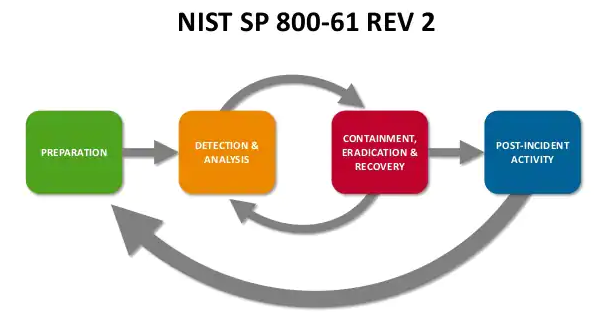
What is an incident response plan?
According to the National Institute of Standards and Technologies, an incident response plan is “The documentation of a predetermined set of instructions or procedures to detect, respond to, and limit consequences of a malicious cyber-attacks against an organization’s information systems(s)”. Incident response plans differ from company to company, which makes it challenging to provide a one size fits all solution.
An incident response plan is “The documentation of a predetermined set of instructions or procedures to detect, respond to, and limit consequences of a malicious cyber-attacks against an organization’s information systems(s)”
Unfortunately, it requires time and effort, but it does not have to be an insurmountable task. In order to design an incident response plan, there are key areas that require attention.
1. Create an incident response policy
This step is normally overlooked but forms the basis of a successful incident response program. The incident response policy is the foundation of the incident response program. The policy serves as the foundational authority and documents the delegated authority and scope. The policy should clearly define what an incident is in order to know when to trigger your incident response plan. The scope of the policy should contain defined objectives to ensure those individuals tasked with incident response know and understand the organizations priorities when dealing with an incident. The policy should also include an incident prioritization scheme to prevent misinterpretations and wrong assumptions.
2. Know yourself
Start off by documentation IR plan requirements and objectives in line with your policy. Consider the impact of regulatory and customer requirements (e.g., POPI, PCI DSS, GDPR) and business objectives (e.g., recovery strategies) The main aim would be to restore systems as soon as possible, but these actions could destroy valuable forensic evidence. Preservation of evidence is a time-consuming process, and you should have a clear understanding of what the intent is of your incident response plan. Your response plan should be clear in terms of preservation and restoration requirements as procedures might differ across your operating environment.
It is vitally important to have a full view of your people, devices, network, workloads, and data. A comprehensive asset register will greatly assist in defining what needs to be protected and how it should be protected. These assets should be classified and ranked in terms of the impact on the organizations ability to meet its business objectives. A classification scheme that defines severity levels is helpful when deciding on a preservation or restoration approach, as well as the restoration timelines, to ensure business continuity.
3. Assemble a Team
There is no hard and fast rule relating to team composition and will be affected by various factors such as geographic reach and location, company size, business sector, sophistication, and data loss exposure of the company. During the establishment, identify each resource, provide full contact information and include a backup person in case the primary contact is not available. Knowing what your Cyber Risk exposure and operating environment looks like will help guide your decisions on team composition.
A critical component of the team will be external incident response management experts. The impact of a security incident can escalate very quickly, and it can be challenging to identify and hire experts to help the company meet breach-related obligations and minimize liability in the heat of the moment. It is advisable to have an external incident response management provider on retainer to assist with the analysis, containment, eradication, and response. This is a highly specialized discipline and can normally not be managed in-house. Involving these teams proactively can help to leverage their expertise and guidance when setting up the incident response process. Response times will be shortened as the provider would have had insight into the business and its operational processes before the incident. In addition to these experts, the following areas can also be considered for inclusion during the establishment of a team:
- Senior leadership representation
- Chief information Security Officer/ Data Protection Officer
- Legal Council
- Information owner
- Human Resources
- Communications resources
- Building/facilities management
- Insurance brokers
4. Incident scenarios
Cybersecurity threats evolve quickly, and it is a constant challenge to keep up to date on the new details. For this reason, it is vitally important to include threat intelligence as part of your security activities. There are a variety of providers that can supply you with threat intelligence feeds, some very costly, but there are many free and inexpensive open-source feeds you can leverage off. By subscribing to feeds specific to the business sector you are operating in, will give valuable insight into the types of attacks and targets you should be focusing on. This data should be mapped to your assets to determine the likelihood and impact such an attack would have on your organization. An incident response plan cannot have a one size fits all approach to different breach categories and needs tailoring to your specific environment. Identify the top threats you are likely to face and develop specific plans around those attack vectors. As the landscape changes, regular reviews should be conducted to ensure your incident response plan still caters for the main attacks your will face. Once different assets and threats are identified, you can define specific scenarios to ensure that the plan and procedures address these incidents
5. Design appropriate processes
Scenarios are used to assess and plan appropriate actions and solutions. The appropriate level of protection ties back to the classification scheme defined in the policy, information in your asset register and the impact on your business operations. As a start, take the top 10 or 20 threats and build out processes to be followed in the event of an incident. It is also advisable to build procedures for common type of events, such as ransomware attacks, website/database denial of service response, Virus/malware response, active intrusion response etc.
Communication plans need to be planned in advance. It is vitally important to define roles and responsibilities to ensure efficient and effective communication on events surrounding the incident. Consider what the escalation process will look like internal and external to your company, how and when will the regulators be informed, communication to affected customers, communication mediums for handling the incident as well as information sharing to vendors and other external interested parties. The communication plan must include input from legal and regulatory staff to ensure the company does not expose itself to possible litigation issues. It is also necessary to determine when it is appropriate and when not to include law enforcement during an incident as it can have positive and negative consequences to the organization.
The data recovery process requires a full technical recovery plan. It goes without saying that a security incident cannot be resolved in a timely manner without a preemptive backup solution. Backups must be scheduled regularly, and the restore process need to be tested regularly to ensure data can be recovered while keeping the integrity of data intact.
The importance of documentation during the incident cannot be overstated. An effective investigation can be undermined if the documentation is poor. Documentation will outlast individuals’ memory and can serve as a record of actions taken for post-event analysis.
6. Post-incident review
Post-incident review is a detailed retrospective analysis of incidents to unpack the incident from start to finish. It provides valuable insight into the different stages of the event, the impacted processes, people and technologies, and the mitigating actions that were implemented. Analysis of each event provides the opportunity to streamline the process and implement changes based on lessons learned, and most importantly, how to prevent similar incidents in the future.
7. Train, Reinforce, Review and Update the Response Plan Regularly
Team members need to be trained on the company cyber security policies as well as incident response processes. Regular tests of the plan must be scheduled to ensure all members of the team understand their roles and responsibilities to better equip them to quickly protect data and resume normal business operations. The response needs to be as automated as the systems and processes used during the incident response. The only way to achieve this is through constant repetition, analysis, and training.
The bottom line is that incident response plans save businesses. It is impossible to predict when attacks will happen, but it is possible to plan for incidents that have a high likelihood of occurrence to ensure the survival of the company.
References
https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-61r2.pdf
https://www.crowdstrike.com/cybersecurity-101/incident-response/incident-response-steps/
https://www.sans.org/white-papers/33901/
https://www.softwaretestinghelp.com/incident-response-service-providers/
https://searchsecurity.techtarget.com/feature/Top-10-incident-response-vendors
https://popia.co.za/
https://gdpr.eu/
https://socradar.io/the-ultimate-list-of-free-and-open-source-threat-intelligence-feeds/
https://digitalguardian.com/blog/50-threat-intelligence-tools-valuable-threat-insights